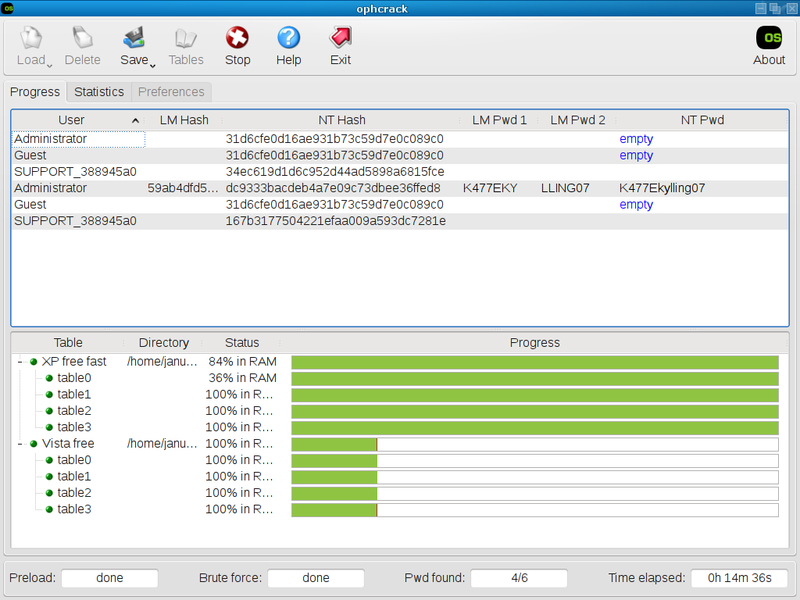
Many computer criminals give out user names and ovens that they obtained illegally. MORE......
"Where do I type that command?" People ask that all the time when they read my early Guides to (mostly) Harmless Hacking.
However, nowadays you might never even hear about telnet, much less use it, unless you are a hacker. So if you are still wondering about telnet, today is your lucky day.
What Is Telnet? Telnet is a protocol that is most commonly used to log into a remote computer. It also is the single most powerful hacking tool on the planet. With just a telnet client program, you can: send email download source code from web sites send unexpected input to webservers that can give you amazing and sometimes interesting results give arbitrary input to many other services on Internet host computers probe the services offered by servers, routers and even people's home computers.
"Where do I type that command?" People ask that all the time when they read my early Guides to (mostly) Harmless Hacking.
However, nowadays you might never even hear about telnet, much less use it, unless you are a hacker. So if you are still wondering about telnet, today is your lucky day.
What Is Telnet? Telnet is a protocol that is most commonly used to log into a remote computer. It also is the single most powerful hacking tool on the planet. With just a telnet client program, you can: send email download source code from web sites send unexpected input to webservers that can give you amazing and sometimes interesting results give arbitrary input to many other services on Internet host computers probe the services offered by servers, routers and even people's home computers.